Cyber Threat Weekly – #11
A busy week in threat news. Let’s start with a new ZLoader variant emerges. An exploration of Telegram’s dark markets and a phishing expedition. Criminals actively target network operator’s credentials. Scanning attempts of Atlassian Confluence RCE Bug.
Discovery and analysis of a new DLL Loader. GitLab releases bug fixes again, one is rated CVSS 9.9 critical. DarkGate malware distributed via Teams group chat phishing. Local privilege escalation bug on major Linux distros.
Large-scale evasive scareware and PUP delivery. The Ivanti zero-day mess continues with new vulnerabilities and active exploitation. Researchers provide technical analysis of APT28 activity. Container RunC bug enables attacker host access.
More malvertising serving a realistic website with malicious download link. New Android Banking Trojan. Docker API used to deploy malware. Windows event log crasher zero-day, unofficially fixed. Mercenary for hire group released new VileRAT variant.
CloudFlare reveals details of November 2023 cyber-attack. Threat actors breached AnyDesk, gained access to production servers. Mastodon bug allows account take over.
Broken Record Alert: Please prioritize patching!!!
Known exploited vulnerabilities continue to be abused by threat actors. We continue to share vulnerabilities with patches available being actively exploited. You can prioritize starting with the CISA known exploited vulnerability (KEV) catalog.
A close #2 priority is those with weaponized proof of concept (PoC) code available. Exploit chances are higher with weaponized PoC code available. If you do nothing else with patching, have an emergency 24-to-48-hour patching process for exploited and weaponized PoC code available vulnerabilities.
Let’s remove some of the low hanging fruit threat actors continue to target.
CISA Known Exploited Vulnerabilities for January 29th to February 4th:
CVE-2022-48618 – Apple Multiple Products Improper Authentication Vulnerability
Allows an attacker with read and write capabilities to bypass Pointer Authentication on Apple iOS, iPadOS, macOS, tvOS, and watchOS.
CVE-2024-21893 – Ivanti Connect Secure, Policy Secure, and Neurons Server-Side Request Forgery (SSRF) Vulnerability
The SAML component that allows an attacker to access certain restricted resources without authentication on Ivanti Connect Secure (ICS, formerly known as Pulse Connect Secure), Ivanti Policy Secure, and Ivanti Neurons.
New 64-Bit Compatible ZLoader Variant
After nearly 2 years, ZLoader is back. This new version has new obfuscation techniques, an updated domain generation algorithm, RSA encryption for network communications, and is now 64-bit compatible.
https://thehackernews.com/2024/01/new-zloader-malware-variant-surfaces.html
https://www.zscaler.com/blogs/security-research/zloader-no-longer-silent-night
https://redcanary.com/blog/msix-installers/
Telegram and Exploring the Dark Markets
How to create a profitable phishing campaign for as little a few hundred dollars. This walk-through shows how dark markets mimic real businesses with ‘free offers’, money-back guarantee, customer support, and more.
Hundreds of Network Operators Credentials Stolen
Over 1,500 victims of credential theft were discovered. This is a perfect case for better cyber hygiene. We must be vigilant and pay attention to the details to minimize impact on our organizations.
https://cybersecuritynews.com/credentials-dark-web/
Active Scanning of Critical Atlassian Confluence Bug
Another group of researchers are picking up scanning attempts to exploit the recent Confluence CVE-2023-22527 disclosed January 16th, 2024. Rated a CVSS:3.1 score of 9.8, exploitation can lead to remote code execution. The correlation of malicious activity is a good thing, we reported similar activity last week.
https://cyble.com/blog/exploitation-of-atlassian-confluence-rce-vulnerability-cve-2023-22527/
New DLL Loader from Blackwood APT Group
Currently targeting users in Japan and China, we’ll keep our eyes open if targeting expands into other geo locations. This one appears to lack malicious intent, but digging a bit deeper shows its true intent. To minimize detection, this loader uses anti-analysis techniques and specific language checks.
https://cybersecuritynews.com/blackwood-apt-escalate-privileges/
https://blog.sonicwall.com/en-us/2024/01/blackwood-apt-group-has-a-new-dll-loader/
Critical GitLab Bug Fixed
With a CVSS score of 9.9, CVE-2024-0402 has been fixed along with 4 other medium vulnerabilities. Just two weeks after the last two critical flaws were fixed.
https://thehackernews.com/2024/01/urgent-upgrade-gitlab-critical.html
https://about.gitlab.com/releases/2024/01/25/critical-security-release-gitlab-16-8-1-released/
DarkGate Threat Actors Social Engineer Victims via Microsoft Teams
Social engineering can be done in so many ways, in this case, since Microsoft Teams allows external connections by default, Teams users are often targeted. We must be careful to minimize ingress traffic to our environments, including instant message chat systems.
Major Linux Distro’s Local Privilege Escalation Vulnerability
This flaw affects glibc, a must have component of virtually every Linux distro. A heap-based buffer overflow, CVE-2023-6246 is identified in the GNU C libraries syslog and qsort functions. A threat allowing a local unprivileged user to escalate to root access.
Researchers Analysis Massive Scareware and PUP Delivery Campaign - ApateWeb
While most will be quick to dismiss, it’s important to understand these campaigns, they can lead to access by more malicious cybercriminals. If it works, it will be commoditized and used by others. This access could also be sold to cyber criminals.
https://unit42.paloaltonetworks.com/apateweb-scareware-pup-delivery-campaign/
Ivanti Releases Fixes and Discloses New Zero-Day Flaws, One Actively Exploited
Wow, this is bad. Active exploitation by multiple threat actors, multiple malwares deployed on exploited devices, over 20 days without patches available. Finally, fixes are released, but also two more vulnerabilities. CISA released the first emergency directive of the year, ordering federal agencies to disconnect Ivanti devices.
Mandiant analyzes multiple web shells and malware.
https://www.mandiant.com/resources/blog/investigating-ivanti-zero-day-exploitation
Researchers Examine a Pawn Storm / APT28 Campaign
From the use of VPNs, TOR, and compromised EdgeOS routers to anonymize traffic to NTLMv2 hash relay attacks and spear phishing, this threat actor is stealthy. There is evidence of sharing infrastructure with cyber criminals to further blend in.
https://thehackernews.com/2024/02/russian-apt28-hackers-targeting-high.html
https://www.trendmicro.com/en_us/research/24/a/pawn-storm-uses-brute-force-and-stealth.html
Leaky Vessels RunC Bug Enables Container Escape
Four vulnerabilities disclosed, the most severe CVE-2024-21626 could lead to container escape. AWS, Google Cloud, and Ubuntu have also released alerts.
https://thehackernews.com/2024/02/runc-flaws-enable-container-escapes.html
https://snyk.io/blog/leaky-vessels-docker-runc-container-breakout-vulnerabilities/
https://aws.amazon.com/security/security-bulletins/AWS-2024-001/
https://cloud.google.com/support/bulletins#gcp-2024-005
https://ubuntu.com/security/notices/USN-6619-1
Malvertising Targeting IT and System Administrators
Malicious ads are being used to lure technology administrators to malicious websites. Analysis shared by researchers shows an interesting pattern, we have seen this over the past several months.
Android Banking Trojan Utilizing Simple RealTime Server
A phishing campaign disseminating this banking trojan. What’s interesting is the use of video streaming to keep tabs on the victim in real time.
Malware Deployed via Docker API
After escaping the container, multiple payloads are deployed including a credential stealer and cryptominer.
https://thehackernews.com/2024/02/exposed-docker-apis-under-attack-in.html
Windows Zero-day Bug Dubbed EventLogCrasher Affects All Versions
Apparently, Microsoft doesn’t see this as a bug that needs immediate attention. It appears to be a duplicate of a 2022 flaw, LogCrusher disclosed by Varonis, still waiting for a patch. The researcher also shared proof of concept code.
VileRAT Distributed by Mercenary for Hire Group
A new variant is being deployed at scale. Stealthy, designed to run in memory with minimal to no disk artifacts, VileRAT is extensible and modular.
https://cybersecuritynews.com/vilerat-attacking-windows-machines/
CloudFlare Cyber Attack Details Released
The attack lasted from November 14th to the 24th, 2023, and was detected on the 23rd. The threat actors analyzed wiki pages, bug database issues, and stole source code.
https://thehackernews.com/2024/02/cloudflare-breach-nation-state-hackers.html
https://blog.cloudflare.com/thanksgiving-2023-security-incident
AnyDesk Cyber Attack
Change passwords and update to the latest version, the old code signing certificate is going to be revoked. Multiple threat actors selling AnyDesk credentials.
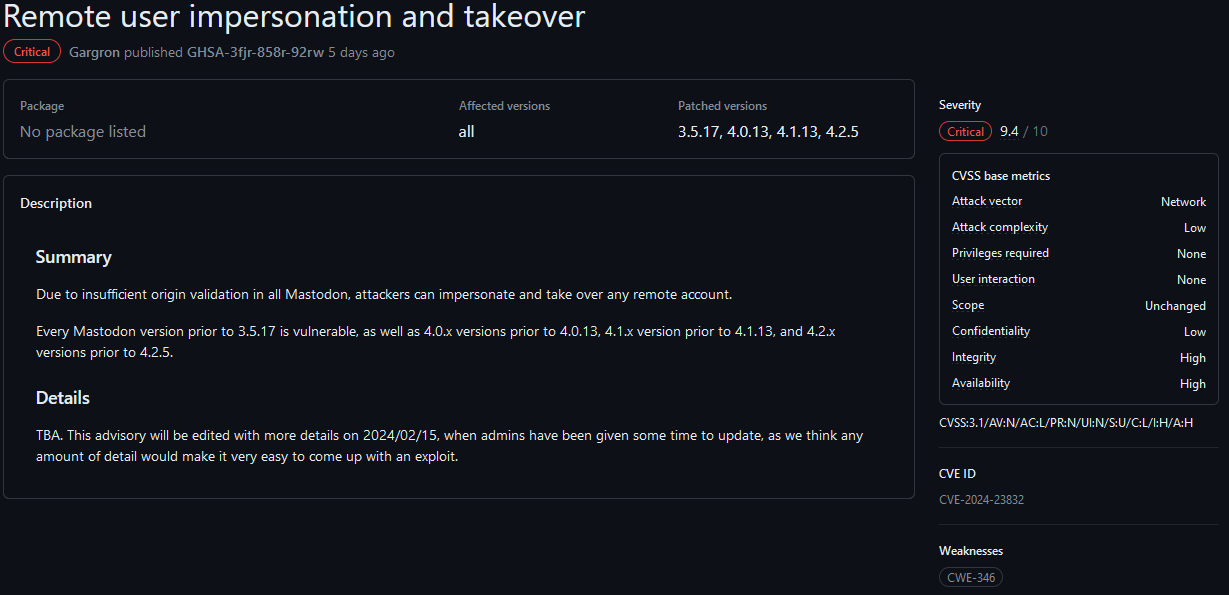
A Critical Mastodon Flaw Tracked as CVE-2024-23832
A critical bug allows for account impersonation and take over. No technical details are available, Mastodon advises details will be available February 15th, 2024.
31337 InfoSec - Cyber Threat Weekly - Derek Krein Newsletter
Join the newsletter to receive the latest updates in your inbox.
Comments
Sign in to join the conversation.
Just enter your email below to receive a login link.
